Govt Abstract
Between December 2024 and February 2025, the LevelBlue MDR staff noticed over a dozen makes an attempt and a handful of profitable intrusions by risk actors (TAs). Internally, we broadly attribute these assaults to the Black Basta ransomware gang. As outlined by different cybersecurity researchers’ reporting of comparable techniques, methods, and procedures (TTPs) noticed; there’s a excessive chance that this exercise is from affiliate teams or preliminary entry brokers. The knowledge introduced under is a compilation of notes, particulars, suggestions, and steerage offered to our clients within the final couple of months ensuing from dozens of opened investigations and incident response engagements. By taking or recommending system and enterprise modifications outlined, organizations can drastically scale back their assault floor, implement a stronger defense-in-depth safety mannequin, in addition to extra shortly detect and thus include an intrusion by this ever-prevalent risk and plenty of others prefer it. Learn the total whitepaper right here.
Preliminary Entry
The TA begins by electronic mail bombing particular customers within the surroundings. This may vary anyplace from a pair hundred to 1000’s of spam and junk emails. They then observe up this exercise by reaching out to those customers through a telephone name or a Microsoft Groups message, with chats named some variation of “Assist Desk”. The TA tells the person that they’ve observed the spam emails and can want entry to their machine to treatment the difficulty. The commonest instrument used to achieve preliminary entry to a sufferer machine is Microsoft’s Fast Help, which is pre-installed on Home windows 10 and better. The TA offers the sufferer a code to make use of when establishing the connection – as soon as enter, the TA can have distant entry to the machine and start establishing persistence after the Fast Help session is ended. In each case the place we noticed the execution of Fast Help, a zipper archive was created throughout the Downloads folder. In reviewing some circumstances, we’ve noticed that the TA has began password defending zip folders containing instruments, however these preliminary information are usually not password protected. Over the last buyer intrusion we responded to, two .cab information had been contained in the zip, and throughout the .cab information had been the authentic OneDriveStandaloneUpdater.exe together with a malicious DLL file to be sideloaded and extra information wanted for lateral motion.
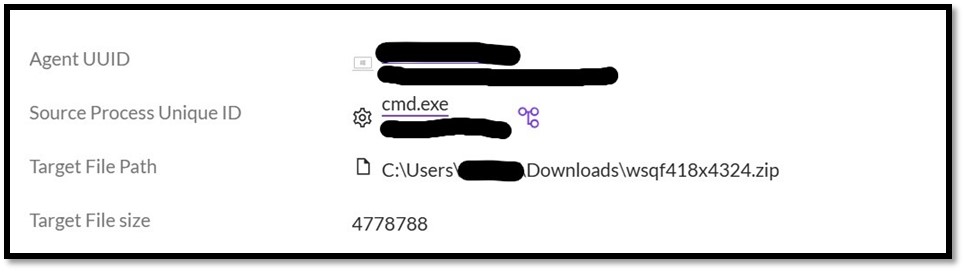
Determine 1: Creation of a zipper archive utilizing cmd exe through the Fast Help session. The TA extracts the information from the archive with tar:
tar xf wsqf418x4324.zip -C "C:Customers[REDACTED]AppDataLocalTemp"
Subsequent, the TA expands the 2 cab information that had been inside:
broaden -i "C:Customers[REDACTED]AppDataLocalTempsymssdifdsook.cab" -F:* "C:Customers[REDACTED]AppDataLocalMicrosoftOneDrive"broaden "C:Customers[REDACTED]AppDataLocalTempdifjsfhcx.cab" -F:* "C:Customers[REDACTED]AppDataLocalMicrosoftOneDrive"
After the 2 .cab information are deleted, the OneDriveStandaloneUpdater is executed from the OneDrive folder and it sideloads wininet.dll from the identical listing. DLL sideloading happens due to DLL search order hijacking – the DLLs of an executable are normally loaded from a selected location or from reminiscence. Nonetheless, if the applying has not specified the placement of the DLL and it’s not in reminiscence, it can load them on this order:
- The listing from which the applying is loaded.
- C:WindowsSystem32
- C:WindowsSystem
- C:Home windows
- The present working listing
- Directories within the system PATH surroundings variable
- Directories within the person PATH surroundings variable
As a result of this specific software doesn’t specify the trail of the DLLs to be loaded, the wininet.dll throughout the OneDrive folder is loaded, placing the malicious code into reminiscence. The DLL sideloading approach with OneDriveStandaloneUpdater.exe has been noticed in each occasion the risk actor was capable of achieve entry through Fast Help. Extra not too long ago, we’ve got seen wininet.dll leveraged and have additionally beforehand seen winhttp.dll. It could even be attainable for the risk actor to additionally use the next imported DLLs:
- KERNEL32.dll
- USER32.dll
- OLEAUT32.dll
- ntdll.dll
- SHLWAPI.dll
- VERSION.dll
- USERENV.dll
- ADVAPI32.dll
- SHELL32.dll
- ole32.dll
- WINHTTP.dll
- RstrtMgr.DLL
- WINTRUST.dll
- WTSAPI32.dll
- bcrypt.dll
- CRYPT32.dll
- RPCRT4.dll
- Secur32.dll
- urlmon.dll
- WININET.dll
- WS2_32.dll
- IPHLPAPI.DLL
With the implant operating and a brand new scheduled job to make sure OneDriveStandaloneUpdater.exe runs on startup, the TA now has one avenue of persistent entry to the sufferer machine and the Fast Help connection is closed out.
Suggestions
- Implement a Microsoft Groups configuration solely permitting whitelisted/federated domains to achieve out to your inner customers. One other step could be to disable incoming and outgoing chats and calls with Skype customers (except wanted for enterprise continuity).
- Take away Fast Help from all end-user machines except explicitly required for enterprise and IT companies. Our clients have been leveraging GPO and CCM to take away the applying, in addition to blocking domains associated to the Fast Help service:
- remoteassistance.assist.companies.microsoft.com
- *.relay.assist.companies.microsoft.com
- Comply with steerage within the Persistence part of this report on stopping the obtain and execution of distant monitoring and administration (RMM) software program, as this TA can have victims obtain different instruments if Fast Help will not be out there.
- Educate customers on this risk vector and supply steerage on processes your inner IT staff will take earlier than reaching out to them (both via Groups or over the telephone), or a verification course of that’s to be adopted. Threats that require the sufferer to repeat and paste instructions, both as a drive-by compromise or through phishing/vishing are on the rise; a consideration right here could be limiting the flexibility of end-users operating instructions in command immediate or PowerShell.
For indicators of compromise in preliminary entry, in addition to a deep-dive into the next levels of a Black Basta assault: Discovery, Credential Entry, Lateral Motion, Persistence, and Exfiltration, in addition to our professional steerage on containment and remediation, remember to obtain our complete whitepaper right here.


